
carloscastilla - Fotolia
What's involved in VPN maintenance and management?
Before an organization's VPN is up and running, IT teams must address four important aspects of VPN maintenance and management to keep abreast of transforming security concerns.
When it comes to the VPN support lifecycle, IT teams must understand VPNs, make technology decisions and know how to integrate a VPN platform into an enterprise network. But that's only the beginning.
Many technology managers are under extreme pressure to get VPNs up and running as quickly and cost-effectively as possible. Once the VPN is installed and running, however, it is generally too late to understand what VPN maintenance and management require on an ongoing basis. This overview examines key areas organizations must address for ongoing VPN maintenance and management, which is true for both remote access and site-to-site VPN connectivity.
IT teams must continuously maintain four critical aspects of VPNs in order for the service to scale and adapt to ever-increasing security requirements of enterprise network traffic. Before IT teams adopt a VPN service, they must address how their organizations will handle the following concerns:
- end-user support
- tunnel architecture
- encryption key management
- hardware and software VPN maintenance
1. End-user support
IT teams need the ability to add or remove users easily using a centralized user database. While teams can create and maintain a separate database for VPN users, it's far easier to tap into an already existing user database, such as Microsoft's Active Directory (AD).
VPN infrastructure can tap into AD with protocols like Remote Authentication Dial-In User Service or Lightweight Directory Access Protocol. Teams can consider this the business's source of truth regarding who can access various network resources, including VPN connectivity.
It also makes employee onboarding and offboarding easier. When technology managers remove an employee from AD, they also revoke VPN privileges. That said, it's also important to verify that the IT staff members who onboard employees understand when to -- and when not to -- enable remote access VPN login services to various employees or vendors.
While teams can use AD to handle authentication and basic access to VPN services, they must enable the VPN platform to permit or deny access to specific segments of the corporate network or to specific ports and protocols. These are known as VPN access lists and are required to permit or deny network admittance for both remote access and site-to-site VPN connectivity.
2. Tunnel architecture
A proliferation of tunnels is required to support enterprise connectivity needs. Most VPN platforms claim to support a finite number of remote access and site-to-site tunnels, but performance degradation can occur before the VPNs reach those limits. VPN administrators must keep a close eye on the number of users and tunnel endpoints simultaneously connecting.
Bottlenecks can easily form within the VPN platform or through depletion of available internet bandwidth. An example of VPN overextension is enterprise needs during the COVID-19 pandemic. In early 2020, as businesses began to let employees work from home, the number of simultaneous VPN connections skyrocketed. While some network architects designed their VPN infrastructures to support higher load levels, others were not so lucky and required emergency changes to increase the number of supported users.
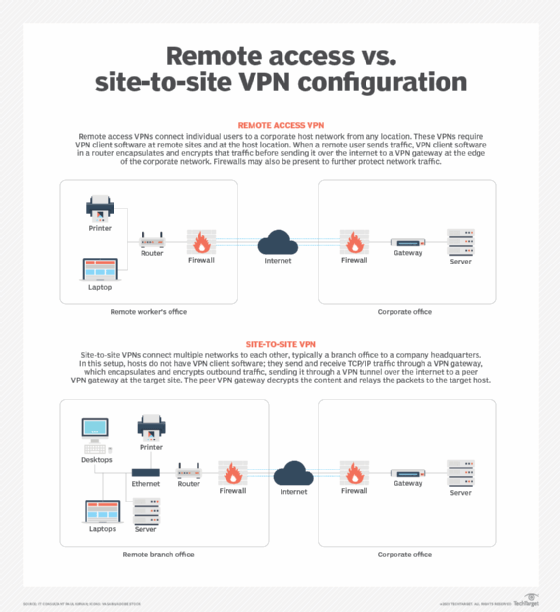
3. Encryption key management
Encryption key management is another important factor from both usability and security perspectives. Ongoing key maintenance can burden teams because they must not only generate, distribute and store keys in a secure fashion, but also update and change keys on a regular basis.
Commercial certificate providers issue public keys, which are commonly valid for anywhere between three months and two years. Once expired, administrators must repurchase and reapply the keys.
Private, pre-shared keys are also popular for site-to-site VPN encryption. Teams should also place these on a fixed renewal schedule to ensure the keys don't fall into the wrong hands. However, changes to these types of keys often require coordination with administrators on the other end of the VPN tunnel, if the tunnel terminates on a third-party network. Thus, for large VPN infrastructures, key management may require a dedicated resource.
4. Hardware and software VPN maintenance
Teams must prepare to handle the hardware and software maintenance of the VPN platform itself. This not only includes VPN head-end server upgrades, but also upgrades to client-side VPN software installed on PCs and smart devices.
For VPN maintenance, teams should address the following questions:
- Can you upgrade the system without causing a service outage?
- Does the system require patches to support new features and capabilities?
- Who is responsible for ongoing VPN maintenance?
- How should you update and patch VPN client software?
End-user support, tunnel architecture, key management, and hardware and software VPN maintenance can influence the cost, resources and time it takes to keep VPN systems up and running. Teams must consider these factors on the front end prior to purchasing a service, and they must build these processes into the operational environment to address them on an ongoing basis.






