DOS (disk operating system)
What is a disk operating system?
A DOS, or disk operating system, is an operating system that runs from a disk drive. The term can also refer to a particular family of disk operating systems, most commonly MS-DOS, an acronym for Microsoft DOS.
An operating system (OS) is the software that controls a computer's hardware and peripheral devices and allows other software programs to function. Early computers of the 1940s and 1950s did not have disk drives. Instead, they were hard-wired to carry out specific computations.
Later, computers were able to store instructions loaded into the computer's memory using punch cards and then, after that, magnetic tapes. Computer memory space was limited, and when the instructions to control a computer were moved onto a disk drive, such as a floppy disk or internal HDD, it was considered cutting-edge technology.
DOS is also used to describe several similar command-line disk operating systems. Early computers, such as the Commodore 64, Atari 800 and Apple II, all featured a disk operating system, including Commodore Business Machines DOS, Atari DOS and Apple DOS, respectively. DOS/360 was an OS for IBM mainframes, which first appeared in 1966, but it is unrelated to the 8086-based DOS of the 1980s.
How does a disk operating system work?
When a computer is powered on it goes through various steps called the boot process. For a computer running a disk operating system, the following six steps are standard:
- The read-only memory (ROM) bootstrap loader reads the Master Boot Record and passes control over to it.
- The boot record loads the disk operating system into memory, and it takes control of the machine.
- The computer transfers data stored on a magnetic disk to its main memory, the random access memory.
- It also transfers data to external devices attached to the computer, such as a computer screen or printer.
- The computer provides various application programming interfaces for programs like character input/output (I/O), memory management, program loading and termination, as well as handling input from the user through a keyboard.
- The OS also provides file management that organizes, reads and writes files on storage. The files are organized in a hierarchical structure of directories, subdirectories and files.
A disk operating system doesn't have a graphical user interface (GUI). Its interface is character-based, so users must type commands in the command line to indicate what actions they want.
DOS features
Among the features and limitations of disk operating systems are the following.
Features
- Command-line interface (CLI). It does not have a GUI and doesn't accept mouse inputs. It is a character-based interface system where all commands are entered in text at the command-line prompt.
- Management. A disk operating system can manage a computer's files, I/O system and its memory.
Limitations
- No built-in security. It does not have built-in security, such as file ownership and permissions.
- No multiusers or multitasking. It also does not support multiusers or multitasking. It is only able to run one program at a time, but it provides direct access to the basic I/O system and underlying hardware.
- Challenging interface. The CLI, in which a user must type in commands, requires the user to remember commands to run programs and do other OS tasks. This approach makes it difficult for novices to use. For example, typing the command cd \directory_name changes the current working directory to the named directory and typing the command dir lists the files in the current directory.
Common DOS commands
MS-DOS is not case-sensitive, so commands can be typed in either uppercase or lowercase. However, other disk operating systems have case-sensitive CLIs. DOS commands include the following.
| Command | What it does | Example |
| cd | Changes directory | Type cd c:\techtarget in the command line to change the working directory to c:\techtarget. |
| cls | Clears all the contents on the screen, leaving only the command prompt | Type cls in the command line. |
| copy | Copies one or more files to another location | Type copy c:\techtarget\file.txt c:\techtarget\file2.txt to copy c:\techtarget\file.txt to c:\techtarget\file2.txt. |
| del | Deletes one or more files | Type del c:\techtarget\file2.txt to delete the file file.txt from the directory c:\techtarget. |
| deltree | Deletes all files and subdirectories from a computer | Type deltree c:\techtarget\drafts to delete the directory drafts, including all files and subdirectories contained in it. |
| dir | Displays a list of files and directories in a directory | Type dir c:\techtarget to display a list of files and directories in the directory c:\techtarget. |
| format | Formats a disk for DOS files | Type format e: to format the disk in drive e: for use with DOS. |
| help | Lists the available commands or more information about a specific command | Type help del to display information about the del command and how to use it. Most commands have optional switches that are explained in the help information. |
| mkdir or md | Creates a new subdirectory | Type mkdir c:\techtarget\drafts to create the subdirectory drafts in the c:\techtarget directory. |
| move | Moves files or directories from one directory to another or from one drive to another | Type move c:\techtarget\file.txt c:\techtarget\drafts\file.txt to move c:\techtarget\file.txt to c:\techtarget\drafts\file.txt. |
| ren or rename | Changes the name of a file or directory | Type ren c:\techtarget\file.txt c:\techtarget\file2.txt to rename the file c:\techtarget\file.txt to c:\techtarget\file2.txt. |
| type | Displays the contents of a file on the screen | Type type c:\myfile.txt to show the contents of the myfile.txt file. |
| * | A wildcard character that represents one or more characters a group of files has in common | Type copy c:\techtarget\*.txt c:\techtarget\drafts to copy all files with the extension of .txt to c:\techtarget\drafts. |
| ? | A wildcard character that represents a single character a group of files has in common | Type copy c:\techtarget\document?.txt c:\techtarget\drafts to copy files named document1.txt, document2.txt and so on to c:\techtarget\drafts. |
History of DOS
The arrival of the microprocessor in the 1970s started a computing revolution, and the market for personal computers (PCs) began to boom. IBM, which was known at the time for its mainframes, released the IBM 5150 Personal Computer in August 1981. To speed up the development of this new computer, IBM decided to license various components from other companies.
Its first choice for an OS was the CP/M-86 software from Digital Research (DR). However, disagreements over nondisclosure agreements and licensing led IBM to choose a CP/M-like OS from Microsoft. Microsoft bought the rights to market 86-DOS, an OS based on the Intel 8086 16-bit processor. 86-DOS was created by Tim Paterson at Seattle Computer Products (SCP) and was originally called QDOS, an acronym of Quick and Dirty OS.
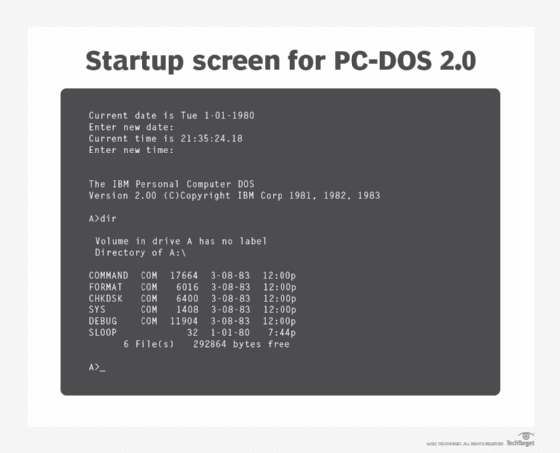
After leaving SCP for Microsoft in 1981, Paterson worked on the PC-DOS version of 86-DOS for IBM's PC. PC-DOS was the first widely installed DOS used in PCs running on Intel 8086 16-bit processors.
Microsoft produced its own almost identical version of PC-DOS called MS-DOS. As the sales of PCs grew, the ubiquity of MS-DOS grew as well. Subsequent versions featured improved performance and additional functionality, such as support for foreign and extended characters and larger HDDs. It also had enhanced memory management, an improved text editor and network support.
When Microsoft first introduced Windows as a GUI for MS-DOS, early users had to type "WIN" at the DOS prompt to launch the Windows program. Windows has since evolved from being a GUI program running under MS-DOS to a full OS taking over as the default OS, though it was not until Windows XP that consumer versions of Windows stopped relying on the DOS program win.com to bootstrap the Windows kernel.
The last retail version of MS-DOS was MS-DOS 6.22, and PC-DOS 2000 was the last retail release of PC-DOS. After this release, MS-DOS was still bundled as part of Windows but no longer required a separate license. It can still be run under Windows using a command processor that emulates the MS-DOS interface. There is an open source version of DOS called FreeDOS that is based on and compatible with MS-DOS. Other versions of these OSes include DR-DOS, ROM-DOS and PTS-DOS (PhysTechSoft DOS).
Because of the many legacy applications, disk operating systems will continue to be in use for many years. They can be used for simple embedded systems, though securing legacy OSes against modern attacks is a concern. These OSes provide machine independence and have no licensing cost in the case of FreeDOS and other open source OSes.
The takeaway
Disk operating systems played a significant role in the early development of personal computing. Today, some 55 years after their initial development, they hold a place as one of the most important types of OSes in the history of computing.
Microsoft recently introduced Windows 11. Find out where the Windows OS is headed and the important role it continues to play in computing.
Note: The acronym DoS with a lowercase "o" is short for denial of service, a method of attacking a networked computer by sending it an abnormally high number of requests in order to exhaust its resources so that genuine users cannot gain access.