SD-WAN vs. VPN: How do they compare?
When comparing SD-WAN and VPN, enterprises choosing between the two technologies should consider factors like cost, management and routing intelligence.
Software-defined WAN is sometimes marketed as an upgraded version of a VPN over the internet. However, many IT teams want to understand at a deeper level the fundamental differences and similarities between SD-WAN and VPN services.
This guide examines those similarities and differences to help IT teams decide which technology is best for their organizations.
What is a VPN?
Encryption is vital for security, as network traffic that travels over an internet connection is vulnerable to interception, manipulation and theft. The types of threats that affect insecure data include the following:
- Man-in-the-middle attacks.
- Cookie theft.
- Evil twin Wi-Fi attacks.
A VPN protects against all these threats. It secures traffic between two points, enabling data to pass between those points securely.
VPN technology was prominent during the COVID-19 pandemic when employees needed to work remotely and share data securely. VPNs acted as a proxy perimeter. A VPN used in remote work scenarios is typically software-based and installed on a device as a VPN client. The other end of the tunnel might be software or a VPN appliance. The VPN encrypts all outbound traffic and decrypts all inbound traffic, creating an encrypted tunnel.
IPsec and SSL VPNs
VPNs use internet protocols as part of the mechanism to encrypt traffic. Below are two common types of VPNs:
- IPsec VPN. The Internet Engineering Task Force developed the IPsec protocol in the 1990s. IPsec VPNs use the protocol to encrypt end-to-end network traffic.
- Secure Sockets Layer (SSL) VPN. An SSL VPN is an alternative to an IPsec VPN. SSL VPNs are based on the SSL or Transport Layer Security internet protocols.
The fundamental mission of an IPsec VPN is to drop authenticated packets. All traffic between endpoints is encrypted at the highest level, forming the basis of a VPN over the internet. VPNs can be simple and cost-effective but can also be problematic in guaranteeing network performance.
This article is part of
What is SD-WAN (software-defined WAN)? Ultimate guide
How a VPN works
A VPN's primary function is to encrypt traffic from Point A to Point B. It isn't designed for any level of intelligent performance optimization.
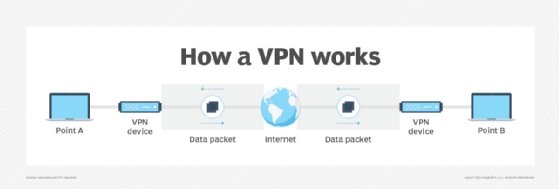
At its most basic level, a VPN prioritizes applications and traffic before they are encrypted. However, when traffic travels within an encrypted tunnel, it won't be prioritized, as the header is encrypted and can't be viewed. The result is a best-effort network that supports traffic at a reasonable performance level.
A VPN can work well for small businesses operating over a single IP backbone. For larger companies with multiple locations, however, an IPsec VPN can cause latency and performance issues with voice and video applications.
Advantages and disadvantages of a VPN
Standard VPNs offer simple WAN connectivity using an authenticated tunnel and encryption. As a result, VPN services are typically simple, low cost and easy to deploy. However, this simple functionality comes with both advantages and disadvantages.
Advantages of a VPN
- Security. A VPN is designed to secure network traffic and offers an easy way for remote workers to safely connect to corporate apps and files from anywhere.
- Safe remote work. Remote and home workers' use of public networks and the internet creates gaping security holes. A VPN encrypts all traffic to prevent interception attacks.
- Privacy. A VPN provides an anonymous IP address. Any traffic communicated via a VPN, including any internet browsing and associated online activity, is anonymized. A VPN under corporate control audits employee site access.
- Ease of installation. VPNs are usually easy to install, and corporate VPNs are typically deployed and managed centrally.
- Cost. VPNs are typically cost-effective and require low maintenance.
Disadvantages of a VPN
- Performance and reliability. A VPN can often be slow, especially if the bandwidth is low, such as on trains or in public areas.
- Security. Employees find ways to circumvent VPN controls when security prevents ease of work. If a VPN slows down work, an employee might find ways to send emails and data and connect to corporate apps using less secure methods. Additionally, a VPN cannot prevent a data breach, such as a breached corporate perimeter due to unauthorized access via a phishing attack.
- Privacy. VPNs do not always block tracking. This leads to a false sense of privacy, which could violate privacy policies.
- Connectivity issues. Some sites actively block access via a VPN. This could prevent employees from performing research and similar activities. Delay-sensitive applications require more management functionality than is available using a VPN. Finally, cloud-based services require optimized internet connectivity, along with advanced next-generation security, which VPNs can't always provide.
- Hidden costs. The use of encryption increases data bandwidth usage and can increase data costs.
What is SD-WAN?
Modern enterprises typically use multiple work environments, including hybrid clouds, remote, microbranches and multibranches. Such a multiplex situation means that workloads and access control are challenging to manage, and poorly configured connectivity can affect performance if users are funneled into centralized management points.
As a result, SD-WAN has evolved to simplify WAN connectivity and improve bandwidth and performance across complex infrastructures.
How does an SD-WAN work?
SD-WAN is based on a virtual WAN architecture that uses software instead of hardware to connect multiple LANs. This means an SD-WAN architecture doesn't require specialized routers. Instead, SD-WAN works by steering traffic via standard internet connections to ensure optimal performance in line with business requirements.
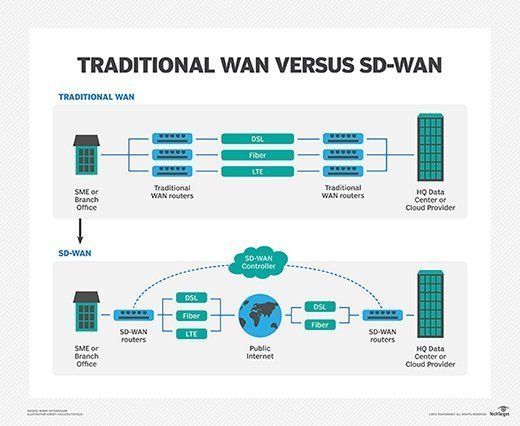
While SD-WAN has a lot of hype around it, the architectural approach has become a favorite for handling the distributed networks of modern enterprises. The distributed and complex nature of these networks requires intelligent traffic analysis to prioritize critical business application use.
One of the positives of SD-WAN is the visibility it provides in distributed networks. This visibility would otherwise be challenging for organizations to achieve. SD-WAN then applies centralized policies to the visible endpoints.
SD-WAN appliances and clients offer an all-in-one, easy-to-use capability. However, the original promise of SD-WAN occurs when each device or client becomes a fast conduit to a centralized management server. In other words, businesses can adjust their use of SD-WAN services to address more complex elements, or whichever elements meet their overall need.
SD-WAN technology continues to evolve and shape new network management and optimization approaches. For example, SD-WAN is also a component of software-defined branch, an architecture designed to centralize the management of the security and connectivity for branch offices.
Advantages and disadvantages of SD-WAN
SD-WAN technology is a strategy that has evolved from enterprises adopting cloud services. As cloud apps and services have become ubiquitous, SD-WAN has stepped in to provide visibility, application awareness, remote access and granular security.
SD-WAN doesn't have end-to-end quality of service (QoS) like a Layer 3 Multiprotocol Label Switching (MPLS) VPN. However, SD-WAN has the capability to sense network conditions and locally prioritize applications.
Advantages of SD-WAN
- QoS. SD-WAN's local QoS is more advanced than basic internet VPN services. This is due to a more granular level of support and capabilities like caching or application acceleration.
- Performance and reliability. Traffic routing is optimized to ensure high-performance levels and reliability. SD-WAN provides improved bandwidth and prioritizes application delivery for users to access public cloud apps from any location.
- Easy to use. An SD-WAN offering that provides simplified self-management with easy-to-use GUIs simplifies SD-WAN installation and configuration. For example, traditional Cisco IOS VPN configuration requires expertise and accreditation, whereas SD-WAN configuration is based on a point-and-click approach.
- Data security. SD-WAN technology provides a VPN and data encryption to protect data during transit.
- Granular policies. SD-WAN enforces routing and security policies on a per-application basis.
- Management. Tasks can be automated with maintenance and upgrades performed centrally.
- Cost-effective. SD-WAN supports any network connectivity, from MPLS to virtual private LAN service (VPLS) and internet VPN. In addition, SD-WAN's application-based routing capabilities use multiple paths, like the internet, 4G or MPLS.
- Reduced costs. SD-WAN doesn't require specialized hardware, which helps minimize Capex.
Disadvantages of SD-WAN
- More costly than IPsec VPN. Currently, it's cheaper to deploy simple IPsec devices to create standard VPN connectivity. However, enterprises get what they pay for, and SD-WAN provides functionality above and beyond an encrypted tunnel.
- SD-WAN deployment and management. Transitioning to an SD-WAN-controlled network can be complex. Organizations should have skilled IT staff to deploy, manage and configure an SD-WAN. However, managed SD-WAN services can alleviate this risk.
- Unpredictable environment. Many SD-WAN providers advocate saving money by using multiple ISP backbones. This strategy makes sense unless a business encounters latency and jitter across applications due to traffic routing via numerous service providers. Multiple ISPs might be fine for national deployments, but global enterprise customers should carefully consider deploying a WAN using the lowest-cost providers within their region.
The differences between SD-WAN and VPN
Now that we've explored the advantages and disadvantages of both VPNs and SD-WAN, let's look at the major differences between the technologies.
SDN capabilities
The main differences between a standard IPsec VPN and SD-WAN focus on the feature-rich offerings of software-defined networking (SDN) on which SD-WAN technology is based. SDN consolidates options into a single platform that is available as hardware with virtualized or client access. Likewise, SD-WAN acts as a collection of different aspects of WAN features consolidated into a single platform with ease of management.
Routing intelligence
Both ends of the VPN transport need to secure traffic, reduce access based on permissions, conduct WAN optimization and select the best path for optimal traffic routing. Standard VPNs generally don't include the intelligence to route traffic based on the most optimal and secure path. That said, some enterprises still need to deploy VPN services without SD-WAN functionality, such as temporary office deployments or locations with simple requirements.
Security
It's important to note that end-to-end VPN encryption is only a small component of overall security. IT teams are responsible for supporting users with remote cloud-based work, partners, productivity applications and more. This complex matrix of users and devices is best secured using zero-trust principles. A swath of security services can be integrated with SD-WAN to provide a comprehensive, zero trust-capable architecture.
SD-WAN can enforce zero-trust security when additional security offerings are integrated across the architecture to prevent breaches. For example, Secure Access Service Edge (SASE) is a unifying architecture that merges the functionality of SD-WAN and security. Integrated alongside a SASE architecture, SD-WAN can enforce the principles of zero-trust security to protect access to resources, no matter where users, devices, applications or workloads are located.
Should you replace a VPN with SD-WAN?
Network teams should base the decision to replace VPN with SD-WAN on clear benefits for adoption. However, many enterprises find that SD-WAN offers significantly more than the WAN connectivity associated with IPsec VPNs. Some of the benefits of moving to SD-WAN include the following.
Management
SD-WAN can manage and report at the network and user levels. In addition, SD-WAN enables enterprises to support and facilitate application access via a single interface in a way impossible with simple VPN services.
Consolidation across functions
SD-WAN can consolidate the LAN, WAN, users, security and application performance into a single platform. This is vital for business transformation and is above and beyond the capabilities of a VPN service.
Business alignment
Alignment to business goals and strategies is necessary when deciding between an IPsec VPN and SD-WAN. Although SD-WAN can empower more extensive enterprise networks, the same enterprise might face end-to-end traffic concerns, especially internationally.
When choosing between an IPsec VPN or SD-WAN, network teams should ask the following questions:
- Does your business need to guarantee application performance, or is the best effort acceptable?
- Does your company use the cloud and support remote, insecure networks?
- Does your company want to manage its own WAN?
A simple router or client with IPsec functionality is acceptable for businesses looking to implement cost-effective, best-effort VPN services using a traditional VPN appliance with a simplified feature set.
Making the decision: SD-WAN or VPN?
While predicting the future is difficult, businesses will always look for the best network performance, security and flexibility for a relatively low cost. Therefore, the choice of SD-WAN or IPsec VPN comes down to the best option, for the best price, under specific use cases.
The objective of SD-WAN is to take business elements and map them to business enablement. The network becomes more granular with SD-WAN, enabling better reporting, security and application performance. Also, SD-WAN can sense network conditions to ensure a predictable level of performance, no matter where a client connects from.
When comparing SD-WAN to a VPN, SD-WAN is far more comprehensive, offering features and functions beyond the capability of a VPN. In addition, SD-WAN technology can enable basic internet VPNs and terminate global MPLS and VPLS networks.
But, when considering any networking technology, enterprises need to be wary of marketing hype that can lead them down a path of buying SD-WAN with the wrap of a particular service provider offering, which can lack critical components.
As time passes, technology accelerates, and product features continue to evolve. Simple VPNs will likely be replaced in the enterprise world by technologies such as SD-WAN.
SD-WAN's superior approach to performance and reliability is likely to win out for enterprises that need to run bandwidth-hungry apps. However, even SD-WAN requires integrated security to ensure that increasingly sophisticated cyber threats do not exploit distributed networks.







