SASE challenges include network security roles, product choice
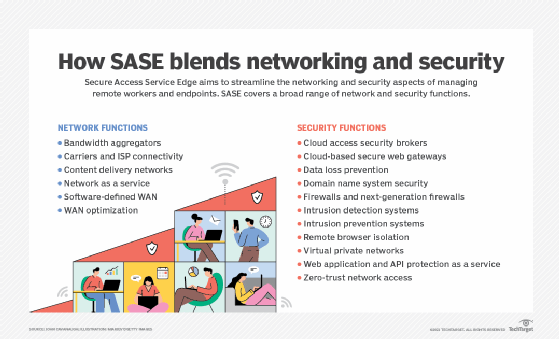
Secure Access Service Edge blends network and security functions. While this integration has its benefits, enterprises still need to address some SASE challenges.
Historically, remote sites were connected by legacy telecom circuits, which connected to a corporate data center, which then connected to the internet and cloud. This setup provided a clear demarcation between IT networking and security teams.
However, the proliferation of dedicated internet access and broadband connections, along with the growth of software-defined WAN (SD-WAN), has created tension among cybersecurity teams and other parts of IT, including networking staff. Cybersecurity teams view these additional internet exposures as an existential threat to their enterprises.
Typical internet access goes through a demilitarized zone (DMZ) with a full stack of security devices and services, including firewalls, data loss prevention tools, and intrusion prevention and detection systems. The enterprise security stack in the DMZ can also use cloud services such as cloud access security brokers (CASBs), content delivery networks (CDNs), distributed denial-of-service (DDoS) protection, and web application and API protection.
Replicating this environment at each remote site would be expensive and difficult to manage. To address this challenge, Secure Access Service Edge (SASE) covers a broad range of network and security functions. SASE was conceived to address the cybersecurity concerns created by SD-WAN. But many vendors are tackling the issue from different backgrounds and perspectives.
SASE challenges hinge on IT team structure
Implementing SASE depends on two major criteria:
- how your IT and security teams are organized and your willingness, or ability, to affect change; and
- the product balance you choose based on criterion No. 1.
Based on these two items -- IT team structure and product choice -- organizations will have to address some key SASE challenges.
SASE challenge 1. The security, systems and networking teams are siloed and will remain that way with full separation.
In this model, the network team operates and manages an SD-WAN with other network-centric systems to protect it, such as DNS protection, DDoS mitigation and CDNs. This means a remote site has one or more tunnels under the network team's control. The security team manages the security portion through the separate cloud-based service, which has its own tunnels.
The downside is an enterprise needs multiple vendors for the service and will probably spend additional money to solve its internal organizational issues.
SASE challenge 2. The security, systems and networking teams are siloed and will remain that way but agree to manage a common infrastructure.
In this model, one or more universal customer premises equipment (uCPE) devices sit at the remote site. But the uCPE maintains role-based access control that enables the network and cybersecurity teams to manage their respective parts of an integrated service.
The downside is managing the competing interests and change controls associated with an integrated platform. But, with its single-vendor approach, at least this model has significant cost savings.
SASE challenge 3. Choosing products.
If your IT teams are siloed and will remain that way with full separation, then a deployment involves at least two products: one or more for networking and at least one for security.
In this example, some networking vendors would include any of the SD-WAN providers, plus the potential need for an additional cloud service for CDN coverage, DDoS protection and WAN optimization. Of course, some of the SD-WAN vendors today incorporate many of those functions. On the security side, some vendors and services would include Zscaler and Fortinet's Opaq Networks offering.
However, if your IT teams are siloed and will remain that way but agree to manage a common infrastructure, then the SASE deployment can combine on-premises services into a single product.
Cisco, Palo Alto and Fortinet are examples of vendors combining their established security systems with SD-WAN and cloud acquisitions to create a roadmap for a full offering. Versa Networks is already there with a multifunction uCPE that has all the local functions associated with SASE and has been working over the past year to add the cloud functions.
SASE challenge 4. Choosing network as a service (NaaS).
Some executives are choosing to avoid the complexity of managing their WANs altogether, and they're looking at a new class of vendors that offers an end-to-end service. You can think of this strategy as NaaS. In this model, the enterprise interfaces with the vendor's client portal to set policies.
Some capable vendors and services in this space include Cato Networks and Fortinet's Opaq Networks unit. Additionally, several emerging vendors, such as Cloudflare, are expanding their CDN business into this space.
SASE vendors evolving quickly
In order to make decisions about a SASE deployment, an enterprise needs to consider its operational policies with its networking and cybersecurity teams and the network and security functions it requires. SASE is about balancing these requirements and risks, but timing is also important. The technology space is evolving quickly, and almost all the vendors are developing integrated offerings.
For example, CDN vendors, such as Cloudflare, are evolving to support NaaS with integrated SASE. Previously, cloud-only vendors, such as CASB leader Netskope, were creating ecosystem partnerships to address SASE.
So, what should you do?
To achieve the cost savings promised by SD-WAN -- and now SASE -- an enterprise should evaluate the savings and look for a reasonably short ROI. With ROIs less than two years, you should proceed. If your ROI is more than two years, you may want to wait and keep an eye on the vendor landscape as it evolves.








