network engineer
What is a network engineer?
A network engineer is a technology professional who has the necessary skills to plan, implement and oversee the computer networks that support in-house voice, data, video and wireless network services.
Although the job titles network engineer and network administrator are sometimes used as synonyms, a network engineer usually has more executive responsibilities than a network administrator. The engineering side deals more with planning, design and technical specifications. The administration side deals mostly with day-to-day maintenance, management and troubleshooting efforts.
The job titles might also differ by education or earnings. Typically, a network engineer has more education and earns more than a network administrator. Employment projections show that network engineers are in demand, and projections indicate the profession -- and other closely related professions -- will grow by about 5% in the next decade.
What does a network engineer do?
Network engineers focus on delivering high-availability network infrastructure to sustain the users' online and on-site IT activities. Network engineers often overlap with other roles, such as computer network architects or security systems engineers, and work internally within an organization or as outside consultants.
Network engineers design and implement network configurations, troubleshoot performance issues, monitor the network and configure security systems, such as firewalls. They often report to a chief information officer, chief information security officer and other line-of-business leaders to discuss and decide upon overall business goals, policies and network status updates. In many situations, network engineers work closely with project managers and other engineers, manage capacity and carry out remote or on-site support.
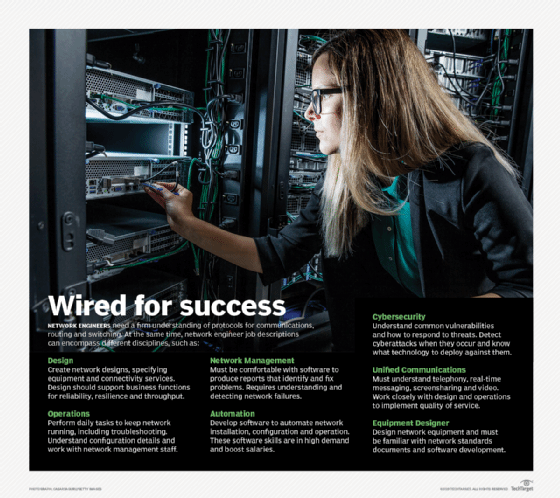
Network engineer skills and qualifications
A job candidate might only need an associate degree to obtain an entry-level network engineering job, but most positions require a bachelor's degree in computer science or multiple years of additional experience. Many network engineers also come from fields such as electrical engineering, physics or mathematics.
Engineers must be able to understand complex networks and pinpoint problems or suggest ways to improve them. They must also be able to work collaboratively, as well as instruct other engineers and support staff to operate the network. And they have to be able to be flexible enough to work with engineers and line-of-business colleagues who might not have any understanding of networking.
In addition to technical skills, network engineers need analytical, leadership, organizational and communication skills. An attention to detail and the ability to fix problems are also important.
Network engineers also now need to know about applications and software development, which reflects the importance of automation and software-defined networking. Engineers need to understand traffic flows, application priority and data transport.
Additionally, engineers should also become acquainted with hyper-convergence, virtualization, security, containers, wide area networking and storage engineering. They should also understand the basic elements of networks, such as clients, servers, internet routing, IP addresses and network hubs.
Network engineer certifications and training
A number of universities and other institutions offer network engineer training courses and programs. Several institutions offer network certifications that can help boost professional credentials.
For many engineers, additional qualifications and training are closely tied to the Cisco engineering certification program, which offers several levels of career training. Other certifications are available from vendors and organizations.
Organizations that offer network certifications include the following:
- Alcatel-Lucent Enterprise.
- Aruba.
- Extreme Networks.
- HPE.
- Juniper Networks.
- Microsoft.
- Riverbed Technology.
- SolarWinds.
- IPv6 Forum.
Some of the more popular network engineer certifications are the following:
- CompTIA Network+.
- Cisco Certified Technician Routing & Switching.
- Cisco Certified Network Associate.
- Cisco Certified Network Professional.
- Cisco Certified Internetwork Expert.
- VMware Certified Professional -- Network Virtualization.
Network engineer salaries
A typical network engineer salary ranges from $65,000 to more than $142,000 annually, depending on skills, experience level and geographic area, according to Glassdoor. The average base salary for a network engineer in the U.S. is more than $95,000 per year, according to Indeed.
Engineers can also earn bonuses, and some employers offer profit-sharing programs as well. Network engineers typically work 40 hours a week, but they might be called upon for weekend work, evenings and other times outside of business hours to fix technical problems.
Specialized roles in network engineering
Network engineers can specialize in several roles and responsibilities, including the following:
- Cloud networking architects assist organizations with cloud infrastructure deployment.
- Local area network engineers install and maintain large LANs for enterprises.
- Network security specialists detect and prevent network security threats.
- Network engineers can also specialize in voice over IP, telecom and data center implementations.
Network engineer career prospects
Network engineers might also pursue different paths within the networking field. Network analysts, for example, specialize in the installation and maintenance of networks and often cross over between the technical and business sides of an organization. Network managers fill a similar role but must train and direct network technicians.
Below is a list of jobs -- besides network engineer -- that are suitable for someone with network engineering skills:
- Network manager.
- Network analyst.
- Network administrator.
- Network specialist.
- Network technician.
- Network architect.
Editor's note: This article was reformatted to improve the reader experience.







