
animind - Fotolia
Achieve network perimeter security through deep segmentation
Firewall effectiveness is in deep decline, but there's still a way to create an effective security perimeter through the practice of deep segmentation. Learn how.
The ultimate end state of software-defined network security is what we at Nemertes Research call deep segmentation. The term refers to the ability to finely control what entities can see, who they communicate with and how they do this, end to end across the enterprise network. With deep segmentation, every physical or virtual switch can enforce security policies and deliver full software-defined network perimeter security and zero-trust architecture.
Formally, a software-defined perimeter (SDP) relies on controllers outside the network to serve as ingress points. An entity that wants to talk on the network has to authenticate with the controller. If it receives authentication, the traffic is redirected to a network gateway, which receives information about who the entity is allowed to talk to.
On the other end, entities already inside the network are only allowed to see traffic from, or send traffic to, entities that have permission to talk to them. SDP merges quite seamlessly with the principles of zero-trust security; combined, they effectively achieve network perimeter security.
Mapping out permissions
Most enterprises may be interested in software-defined network security, but they face challenges putting SDP into production because they don't know what or who should be able to talk to what. Developing that detailed self-knowledge requires robust network analytics and identity and access management (IAM) systems. Analytics helps find all the nonhuman entities communicating on the network, while IAM systems identify both humans and other entities recognized by the enterprise.
Once IT has this knowledge, it possesses a base of well-authenticated people and systems. From here, it can map out which entities talk to which, when they can do so and what protocols are used for transactions. With this map, IT can then more easily assess where it can tighten boundaries around system groups.
A Cloud Security Alliance representative explains the
CSA's software-defined perimeter project.
Further, IT can assign who must talk to whom, rather than who does talk to whom. This is the principle that guides zero trust -- though perhaps zero trust is better described as "verify and then trust," as it's more like zero assumed trust. At this point, all trusted entities are defined and verified.
The shrinking of access ranges improves security. When threat surfaces shrink, so does the risk of both the initial compromise and additional land-and-expand attacks. In fact, IT can craft policies to redirect suspect traffic to honey pot networks, where exploits can be allowed to succeed in order to facilitate forensic analysis and pursuit of the attackers.
How to achieve software-defined network perimeter security
When deploying an SDP system, enterprises should practice a form of land and expand, beginning with the establishment of a network perimeter around a subset of systems, preferably new ones. With a new system, IT can more easily distinguish between an entity with an assumed need for access -- based on its historical access to other systems -- and an entity that has an actual need to access the system in order to do its own work, or to help the new system do its work. IT can spread the protection around all systems eventually by working outward from systems inside the SDP to systems that talk to them.
Of course, not all users and systems are on the enterprise's physical network. But to achieve network perimeter security, IT will still want to apply policy, both to entities not on the company network and to entities working with systems not in the network. For example, IT would want to establish policies for mobile workers reaching out to key SaaS systems or to applications running in an IaaS platform.
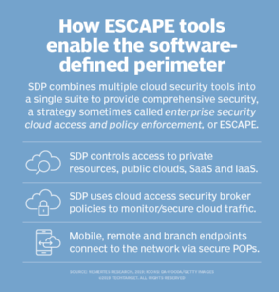
That is where a new class of tools comes into play: enterprise secure cloud access and policy enforcement (ESCAPE) systems. ESCAPE tools combine the functions of virtual private networks and cloud access security brokers. Using ESCAPE tools, IT can deliver a policy enforcement environment -- beginning with secured access to cloud and in-house systems via a VPN client on a laptop, device or virtual machine in a different cloud -- by connecting to a cloud access gateway that can enforce security policies.
As IT security and networking evolve to reflect granular control of network access, based on the principle of verify then trust, software-defined network perimeter security will become the new status quo.








