
itestro - Fotolia
ExtraHop intros Reveal(x) cybersecurity analytics software
ExtraHop fortifies its packet capture platform with cybersecurity analytics software, Reveal(x); Mist introduces a virtual network assistant powered by artificial intelligence.
ExtraHop Networks has added a new layer of cybersecurity analytics software to its IT performance monitoring platform. The new software, Reveal(x), provides anomaly detection of east-west and encrypted network traffic at wire speed, the company said.
Reveal(x) combs through wire data, using a cloud-based machine learning engine to detect malware and unearth other potential issues, said Matt Cauthorn, vice president of security at Seattle-based ExtraHop. The cybersecurity analytics software tracks such things as lateral movement of traffic, command-and-control traffic, and large file transfers. It also scans for unusual access patterns.
"Today's cybersecurity measures lag modern threats because security teams are drowning in alerts, relying on outdated threat signatures and inadequate data sets," Cauthorn said. "In order to protect critical assets we must change what, how, and when we see and investigate threats." Reveal(x), he said, "gives [security operation] teams complete visibility of everything that touches the network, immediately flags anomalies that pose a threat and automates the investigation of these threats."
Cauthorn said Reveal(x) only issues alerts in the event of "meaningful" incidents occurring on critical assets. The alerts, he said in a blog post, include associated background and contextual data -- information that can help reduce the time necessary for a security analyst to investigate an incident.
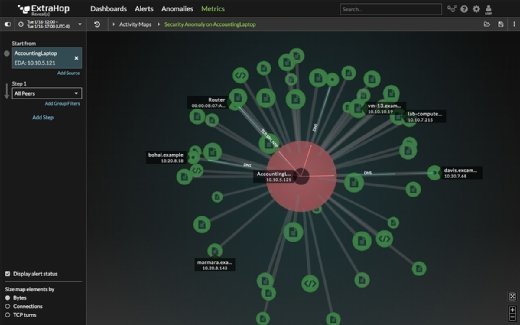
The software uses live activity maps -- part of ExtraHop 7.0, which was released last fall -- to indicate traffic patterns in real time. The new product also replays transactions to let security analysts determine more information about a particular incident's timing and scope.
Reveal(x) is available in three versions of cybersecurity analytics software, with the most comprehensive -- Ultra -- tailored for those organizations with more demanding forensic and compliance requirements.
Mist adds virtual network assistant
Wireless networking vendor Mist has introduced a virtual network assistant, or VNA, that allows organizations to use plain English to track wireless performance across their networks.
The VNA, available in March, uses natural language processing to make it easy for IT staffers to determine problems or to query Mist's cloud-based analytics servers to get additional information about mobile users. The assistant is powered by Marvis, Mist's artificial intelligence engine, said Jeff Aaron, Mist's vice president of marketing.
Marvis lets IT staffers use common phrases -- instead of arcane code -- to determine a performance problem, like asking "Why Bob's smartphone is having a problem," the company said.
Problems addressed include duplicate addresses, packet loss and wireless LAN interference issues.
In the future, Mist, based in Mountain View, Calif., said Marvis would be used for other initiatives, including asset visibility and to determine user engagement with Bluetooth Low Energy technology housed within Mist's access points.
Mist, which rolled out its cloud-managed Wi-Fi service last year, now has more than 200 customers, including Delta Air Lines and Major League Baseball.
Check Point appliance tackles fifth-generation attacks
Check Point Software Technologies has released upgraded versions of its Smart-1 security management appliances, engineered to combat fifth-generation cyberattacks.
The company, based in San Carlos, Calif., introduced three new models, with the most powerful capable of registering up to 100,000 logs per second and securing more than 150 web gateways. The appliances enable centralized and unified policy management, and feature advanced log and threat analysis, the company said.
Fifth-generation attacks, known as Gen V threats, are large-scale and fast-moving attacks that occur across mobile, cloud and on-premises networks. The new attacks can outmaneuver conventional static detection-based defenses. The Smart-1 gear, which can store up to 48 TB of management data, are more than eight times more powerful than previous models, the company said.
The models probe for attacks by correlating, storing and analyzing data across network devices. Information is routed back to a console, where technicians can monitor compliance, generate reports and keep tabs on network traffic.
"The Smart-1 Appliance family gives customers an agile, high-capacity security management solution that delivers in-depth visibility into their security posture," said Gabi Reish, Check Point's vice president of product management and product marketing, in a statement. "This makes it even easier for organizations to keep themselves fully protected against Gen V cyberthreats, by deploying and managing security with unrivaled performance, all on a single device."







