VPN vs. zero trust vs. SDP: What's the difference?
For strong network security, many vendors say VPNs don't cut it anymore. Enter the zero-trust security model and SDPs.
To create a secure tunnel from one point to another or to make resources invisible to outside threats may seem like scenarios that require magic; in reality, they just need network security.
So begin the stories of VPNs, zero-trust security and software-defined perimeter (SDP), three varying elements of corporate cybersecurity with a shared goal of securing company resources. While VPNs have historically had a place in most network security plans, zero trust is a relatively new concept that aims to fill in the security gaps traditional security approaches miss. An SDP is a network architecture that implements zero-trust principles to provide more secure remote access than VPNs.
Many experts predict VPNs will eventually become obsolete as zero trust and SDP adoption grows. For now, however, VPN use remains widespread.
Despite the differences among VPN vs. zero-trust security vs. SDP, a shared goal of securing corporate networks ties the technologies together, as does the increasing need for remote work support among organizations.
Defining VPN, zero trust and SDP
VPN
VPN stands for virtual private network. This technology encrypts tunnels between corporate networks and authorized end-user devices. With a VPN, remote employees can access network resources as if they were in an office and directly connected to the corporate network. VPNs enable secure remote access for employees, regardless of their physical locations.
An organization may deploy VPN technology if it has a significant number of remote users or if it has more than one location for company resources to which employees require secure access. However, VPN shortcomings include a lack of support for diverse types of modern devices, such as IoT and mobile devices, that require network access.
Zero trust
Zero trust is a high-level cybersecurity strategy that treats every user and device as a threat until proven otherwise, limiting lateral movement and denying access requests by default. A zero-trust model upholds the principle of least privilege, which means users and managed devices have permissions to access only the apps, services and systems they need to do their jobs. Zero trust also means users and devices must undergo continual authentication as they move throughout an IT environment, even if they are internal users who have previously accessed a given resource.
Zero trust considers context, as well as identity. For example, zero-trust network access (ZTNA) technology -- which applies zero-trust principles to a remote access architecture -- might deny an authorized user who usually logs in to an application in New York between 9 a.m. and 5 p.m. but suddenly tries to log in from Alaska at 3 a.m.
As it is a philosophy or strategy -- not a single architecture, technology or product -- implementing zero trust can be challenging and complex. Since a zero-trust strategy hinges on identity and access control, teams must also ensure user permissions and authorizations are always up to date and accurate.
Organizations that handle highly classified or sensitive data have the most to gain from a zero-trust approach, although experts say everyone can benefit from it.
SDP
SDP is a network architecture that applies zero-trust concepts to enable secure remote access. It is an overlay network -- a network that sits atop another network connected with virtual or logical links -- that conceals network resources within a perimeter. Attackers and unauthorized users are unable to see or access the concealed resources, as the SDP acts as a cloud or an invisibility cloak to secure network resources.
SDPs use controllers to authenticate and connect authorized users to corporate network resources or applications through a secure gateway, based on identity policies, regardless of where the resources live -- in private data centers, the cloud, etc. An organization may deploy SDP technology to reduce network-based attacks, which include denial-of-service or man-in-the-middle attacks.
Many experts use the terms SDP and ZTNA interchangeably, with some referring to ZTNA as SDP 2.0.
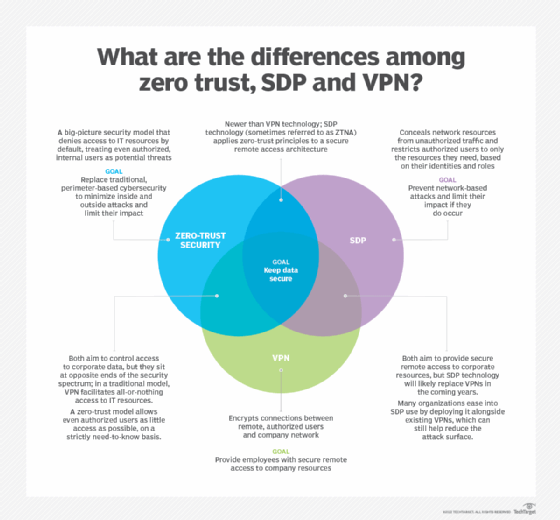
VPN vs. zero trust
VPN and zero-trust capabilities exist on opposite sides of the cybersecurity spectrum. VPNs take an all-or-nothing approach, with authenticated users allowed to roam widely throughout the network, setting the stage for lateral attacks. In other words, if bad actors can just make it past the moat, or VPN, then they have the run of the castle, or corporate network.
Zero-trust security, on the other hand, gives even authorized and authenticated users limited access to resources on a strictly need-to-know basis. If attackers do manage to get inside an IT environment, zero-trust microsegmentations restrict their ability to move laterally and access sensitive data.
While experts agree a zero-trust model provides better outcomes than traditional perimeter security, it's possible for an organization to start implementing zero-trust capabilities, while still using a VPN. For instance, microsegmentation can mitigate some of the risks inherent to VPN use.
SDP vs. zero trust
Zero-trust security is a high-level security philosophy or strategy, with SDP and ZTNA falling under the broad zero-trust umbrella.
SDP and ZTNA architectures apply zero-trust principles and policies to remote network access. These platforms use trust brokers -- software that performs authentication based on identity and context -- to control users' access to applications, services and systems.
As newer network security strategies, SDP and ZTNA have shorter track records in the enterprise than traditional VPNs, but they also offer more innovative defense mechanisms. As cyber attacks increase in volume and sophistication, zero-trust principles -- as applied via SDP and ZTNA technologies -- can help organizations better and more reliably protect their networks from both internal and external threats.
The zero-trust model will likely shape the future of enterprise cybersecurity. An SDP is one way to implement its principles.
SDP vs. VPN
Vendors have touted that VPNs are irrelevant and SDP is the future of corporate network security. But, while most experts agree SDP technology improves upon VPN's capabilities and resolves a number of its shortcomings, traditional VPNs remain central to many organizations' secure remote access strategies. The proposition to rip and replace VPNs with SDPs is also a cost -- both money and time -- many organizations aren't ready to incur.
Still, analysts anticipate that SDP and ZTNA will become increasingly dominant network security technologies in the coming years. As they shift to zero-trust models, many organizations are deploying ZTNA or SDP platforms in parallel with VPNs, easing the transition. By introducing SDP technology for some high-risk use cases, while maintaining a traditional VPN for others, an enterprise can shrink the network's attack surface without ditching the legacy technology altogether.






