microsegmentation
What is microsegmentation?
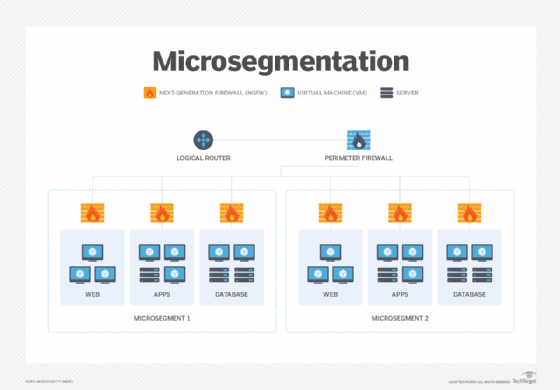
Microsegmentation is a security technique that splits a network into definable zones and uses policies to dictate how data and applications within those zones can be accessed and controlled.
Unlike network segmentation, which requires hardware and is geared to north-south traffic -- that is, client-server data flows between data centers -- microsegmentation relies on software and is tailored to east-west traffic, or server-to-server data flows between applications.
Microsegmentation breaks the network into smaller pieces and limits the type of traffic that can laterally traverse across the network. It can be applied throughout the network, across both internal data center and cloud environments. Microsegmentation enables security teams to dictate how applications or workloads can share data within a system, which direction the data may be shared and whether security or other authentication measures are required.
Objects that can be defined as segments within microsegmentation include the following:
- Workloads. A workload is a specific projected amount of capability for an instance -- each time a specific program or application runs, it is considered an instance.
- Applications. Applications are software programs that run on a computer, in a cloud or on a virtual machine (VM).
- VMs. VMs are computers that contain all the basic components to run but do not have physical hardware, instead they exist within the framework of another existing computer.
- Operating systems (OSes). A computer's OS is its fundamental software on which all other software is able to run.
How does microsegmentation work?
Microsegmentation uses software policies instead of hardware configurations, firewalls and virtual local area networks (VLANs) to manage and create the logical units. The policies dictate how secure zones are created and how subsets are accessed and determine how users and applications can connect to and access only the resources and services they need.
Microsegmentation can be implemented in a variety of ways, with next-generation firewalls (NGFWs) being the most common. NGFWs offer visibility across each layer of the Open Systems Interconnection model, enabling companies to build a logical access control policy around each application that runs across a network. Microsegmentation is also increasingly offered as part of software-defined wide area network product suites, where it can then be deployed to branch and remote sites. Microsegmentation can also be deployed through fabrics, hypervisors and agents.
Microsegmentation use cases
Microsegmentation enables administrators to create customized security policies tailored to individual subnetworks. The technique reduces the risk that an organization's entire network would be compromised in the event a microsegment is infiltrated and prevents lateral movement attacks. Any attack or security breach would be limited to only that particular subnetwork -- not the entire system.
Microsegmentation provides a granular view of network traffic and gives administrators greater visibility and control over the data that flows across network devices. Microsegmentation can be used to identify traffic that might require preferential treatment or management, such as data that must be protected to comply with regulations or standards. Microsegmentation also integrates easily with sophisticated security models, such as zero-trust networking, which requires the verification of users' identities before they can access any device on the network.
Types of microsegmentation
The following are the four general types of microsegmentation:
- Application. Microsegmentation restricts access to data contained within applications, thus protecting highly sensitive data or data that must be specifically handled for regulatory compliance purposes.
- Tier. Microsegmentation is used to separate and isolate the components that constitute an application -- for example, web server, application server and database. This prevents an unauthorized user from moving across the various tiers and allows only those whose roles permit it to access the specific components.
- Environmental. Development, testing and production environments reside throughout the network, both on premises and within the cloud. Microsegmentation keeps each environment separate from the rest, restricting communications.
- User. Microsegmentation relies on user identity services, such as Active Directory, to determine which groups or individuals have access to applications and services. This lets individuals within a VLAN have their own specific permissions.
Benefits of microsegmentation
Once successfully implemented, microsegmentation can yield a variety of benefits, including the following:
- Once the individual parts of a system's infrastructure are secured, it is simpler to maintain the overall health and security of the system because each segment can be maintained on a smaller scale.
- Problem areas or overloaded workflows can be isolated and addressed.
- Gaps among cloud, container and on-premises data centers are eliminated.
- It is much less likely that a virus or malware infects an entire network because each part of the network is outfitted with checkpoints and secure boundaries. Essentially, even if attackers compromise one part of a network, they are not be able to use the compromised access to reach any other part.
- By reducing the network attack surface, companies make their networks more secure.
- Microsegmentation pairs enforcement policies to specific workloads rather than network hardware. These policies are largely automated, can accompany individual workloads wherever they travel throughout the network and can adapt automatically to any changes in the infrastructure.
- IT gains greater flexibility in how workloads are secured. Microsegmentation gives companies the ability to write a single, consolidated policy to manage access, security and theft detection and mitigation that automatically adapts, regardless of changes in infrastructure.
- Mistakes and oversights are reduced because firewalls and routers no longer have to be manually configured to accommodate changes or upgrades to a company's security infrastructure.
- Microsegmentation as an architectural model helps lay the foundation for a zero-trust security model, where traffic is limited based on the principle of least privilege.
Challenges of microsegmentation
Implementing microsegmentation requires consistency and proper planning and can introduce the following challenges:
- Rules must be constantly reviewed to ensure they are appropriate.
- Performance must be analyzed to ensure objectives are met.
- Changes in traffic patterns or the introduction of new applications must be noted and addressed. Not every application, particularly performance-sensitive applications, may be suitable for microsegmentation.
- Microsegmentation is complex. Modeling application behavior and accounting for workloads are critical; otherwise, connectivity and availability problems can occur.
- Support is critical. A successful microsegmentation strategy requires support from multiple groups throughout IT, including the computing, networking, cloud and security teams. Clear understanding, communication and interaction are essential.
Microsegmentation is becoming an increasingly popular tool for organizations seeking ways to improve network security. Workloads and resources now reside in multiple locations -- both internally and externally -- and microsegmentation enables companies to maintain comprehensive security policies throughout their networks.
For more on the zero-trust security model, read the following articles:
What is zero-trust network access? ZTNA basics explained
7 steps for implementing zero trust, with real-life examples
Top 6 challenges of a zero-trust security model
The 5 principles of zero-trust security
The history and evolution of zero-trust security
The difference between firewalls and microsegmentation
Firewalls are an outgrowth of the client-server network architecture model and protect users by inspecting every packet that enters and leaves a network. They use a predefined set of rules to determine if packets are dangerous or not. If a malicious packet is found, the firewall keeps it from entering the network.
Firewalls have become more sophisticated to meet the demands of modern networks. In addition to investigating packets, modern firewalls can now track traffic over time, provide application layer filtering and perform deep packet inspection, among other capabilities. NGFWs feature advanced intrusion protection systems and can use external intelligence sources to more accurately pinpoint potentially malicious traffic.
Firewalls encompass individual networks or users and cannot be extended to external data centers or clouds.
Microsegmentation uses a completely different approach. It divides a network into definable zones and then uses policies to determine who can access assets that are contained in each zone. It focuses on server-to-server traffic rather than client-server. Microsegmentation can also be used in both internal and external settings, regardless of where applications or services may be stored.





