ingress filtering
What is ingress filtering?
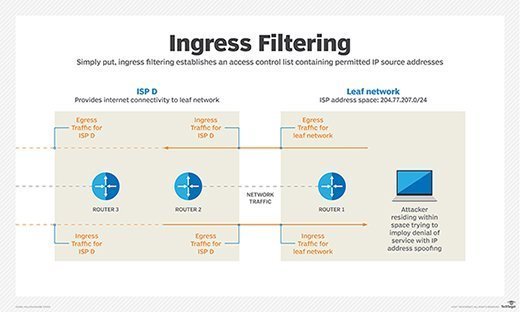
Ingress filtering is a method used by enterprises and internet service providers to prevent suspicious traffic from entering a network. When configured on an edge device such as a router or firewall, ingress filtering examines all inbound packets and permits or denies entry to the network based on information in the packet header. It is a form of packet filtering.
Ingress traffic filtering is one of the first lines of defense in a network security strategy. It intends to prevent cyber attacks, particularly denial-of-service (DoS) attacks that use IP address spoofing.
IP spoofing and denial-of-service attack prevention
At its simplest, ingress filtering involves establishing an access control list that contains IP addresses of permitted source addresses. Conversely, the access control list might also be used to block prohibited source addresses.
Ingress filtering takes advantage of the data link layer IP address filtering capability of a router at the network's edge and blocks traffic that has a high probability of being malicious. It makes this determination based on whether the contents of an IP packet header meet defined criteria.
The packet filter examines several attributes, most notably in this case the source IP address. If the source address is invalid -- that is, if it doesn't match its originating network -- the filter determines the address is forged, or spoofed, and drops the packet.
Ingress filtering is also a feature on switches, which means it can filter traffic on virtual LANs (VLANs) to prevent malicious activity within a private network, such as VLAN hopping. In VLANs, ingress filtering will discard frames whose port is not a member of the VLAN it is trying to access.
How ingress filtering works
Source IP addresses that are commonly blocked with ingress filter include the following:
- Internal IP addresses. Prevent attackers from spoofing internal IP addresses to take advantage of a poorly written firewall rule.
- Private IP addresses. Prevent malicious traffic coming in from an improperly configured internet-based host or an attacker's spoofed address.
- Loopback IP addresses. Prevent traffic from an attacker who is spoofing a loopback address to take advantage of a poorly written firewall rule base.
- Multicast IP addresses. Prevent undesired multicast traffic that is likely to be spam.
- Service or management IP addresses. Prevent attackers from using the public internet to gain unauthorized access to network services running at the network application layer and above.
Additionally, network administrators might want to allowlist traffic from specific regions of the world that their organization does business with or blocklist dangerous regions of the world that their company prefers to not access its environment. There are several free and subscription-based services that can be used to create access control lists for network border routers.
Ingress filtering vs. egress filtering
Ingress filtering is one type of packet filtering. Its counterpart is egress filtering, which examines outbound traffic and only enables packets to leave the network if they meet predetermined policies set by an administrator.
Egress filtering can prevent malicious activity, such as infected machines attempting to leak data to remote hosts, or to block legitimate users from accessing prohibited services, such as online gaming sites.
Editor's note: This article was republished in February 2023 to improve the reader experience.






