secure access service edge (SASE)
What is secure access service edge (SASE)?
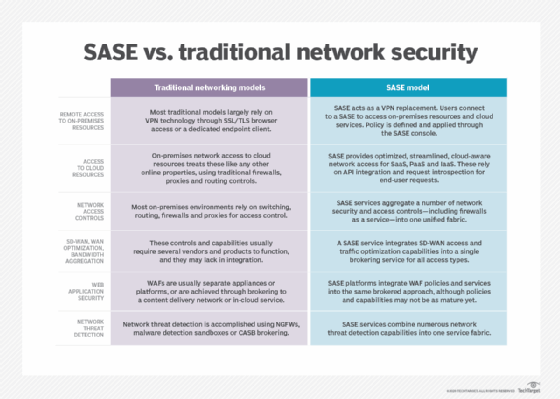
Secure access service edge (SASE), pronounced sassy, is a cloud architecture model that bundles together network and cloud-native security technologies and delivers them as a single cloud service.
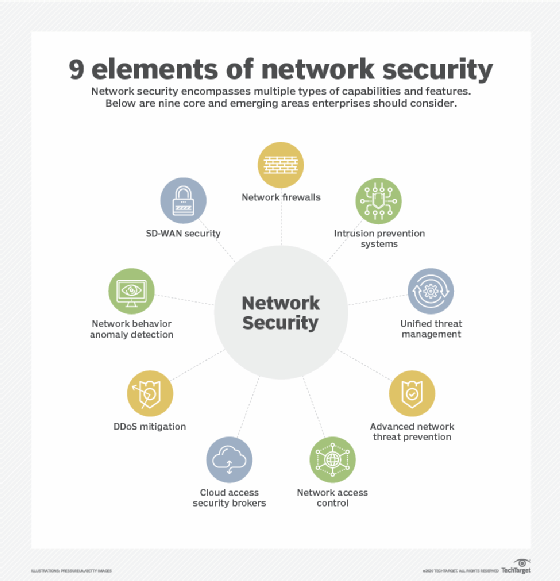
SASE lets organizations unify their network and security tools in a single management console. This provides a simple security and networking tool that's independent of where employees and resources are located. SASE requires little to no hardware and uses the widespread connectivity of cloud technology to combine software-defined wide area network (SD-WAN) with network security functions, including the following:
- Firewall as a service (FWaaS).
- Software as a service (SaaS).
- Secure web gateways (SWGs).
- Cloud access security brokers (CASBs).
- Zero-trust network access (ZTNA).
With the number of remote workers increasing and organizations using cloud services more often to run applications, SASE offers a convenient, fast, cost-effective and scalable SaaS product for networking and security.
How does SASE architecture work?
SASE platforms bundle multiple elements -- SD-WAN with network security measures, such as FWaaS, SWGs, CASBs and ZTNA. The result is a multi-tenant, multiregional platform for security that's unaffected by the locations of employees, data centers, cloud services or on-premises offices.
A SASE platform doesn't rely on inspection engines in data centers. Instead, SASE inspection engines are brought to a nearby point of presence (POP). A SASE client, which could be a mobile device with a SASE agent, an internet of things (IoT) device, branch office equipment or a mobile device with clientless access, sends traffic to the POP for inspection and forwarding to the internet or across the central SASE architecture.
SASE services have the following four defining traits:
- Global SD-WAN service. SASE uses an SD-WAN service with a private backbone, which avoids latency issues from the internet and connects the individual POPs used for security and networking software. Traffic rarely touches the internet and only does so to connect with the global SASE backbone. SASE connects and helps protect all physical, digital and logical enterprise edges.
- Distributed inspection and policy enforcement. SASE services don't just connect devices; they protect them. Inline traffic encryption and decryption are table stakes. SASE services should inspect traffic with multiple engines that operate in parallel. Inspection engines include malware scanning and sandboxing. SASE should provide other services as well, such as domain name system-based protection and distributed denial-of-service protection. Regulations, such as the General Data Protection Regulation, should be enforceable in the SASE's routing and security policies.
- Cloud architecture. SASE services should use cloud resources and architectures with no specific hardware requirements but shouldn't include service chaining. Software should be multi-tenant for cost-effectiveness and able to instantiate for rapid expansion.
- Identity-driven. SASE services have access based on user identity markers, such as specific user devices and locations, as opposed to the site.
Organizations looking for a more advanced user-centric network for their company network management needs could benefit from exploring SASE architecture. Due to the adoption of cloud services, mobile workforces and edge networks, digital and cloud transformation are changing the way organizations are consuming network security. In the past, organizations consumed their security through legacy hardware networks and an outdated security architecture mindset.
Why is SASE important?
As organizations increasingly adopt cloud applications and services, many are quickly learning that network and cybersecurity aren't so simple. Traditional network security protections were built on the idea that organizations should send traffic to corporate static networks, where the necessary security services were located. This was the accepted model, as the majority of employees worked from site-centric offices.
The concept of user-centric networks has changed traditional networking. Over the past decade, there has been an increase in the number of people working remotely from home around the world. As a result, the standard hardware-based security appliances that network administrators used are no longer adequate for securing remote users and their network access.
The importance of SASE can also be seen in edge devices. Automobiles, refrigerators, web cameras, IoT devices on industrial product lines, smart health monitoring sensors and other gadgets are connecting to enterprise networks and sharing data. Since every edge device serves as a potential entry point for a cyberattack, edge security is crucial. SASE provides a method for securely connecting edge devices and protecting the data they exchange.
SASE also enables companies to consider security services without being dictated by the whereabouts of company resources, with consolidated and unified policy management based on user identities. This shifts the question from "What is the security policy for my site or my office in New York?" to "What is the security policy of the user?" This change creates a major shift in the way companies consume network security, enabling them to replace several different security vendors with a single platform.
Uses of SASE
Organizations that adopt SASE are adapting it for areas and uses such as the following:
- Data protection. SASE offers increased visibility into a network, while also providing a stack of security tools for threat protection.
- Endpoint security. SASE provides cloud and WAN security at an organization's endpoints. It also brings network and endpoint security together in one platform.
- Remote and hybrid work. Organizations that have adopted remote or hybrid workstyles and use SD-WAN to enable employees to access their network can be more secure and cost-effective by moving to a SASE platform instead.
- Networking and IT. As SASE integrates both networking and security features, it can aid IT and network teams in managing the network.
- Connecting main and branch locations. SASE provides secure access to networks in both an organization's main and branch locations, providing consistent policies between locations.
What are the benefits of SASE?
The cloud-based approach of SASE offers the following benefits for network security:
- Ease of use. One management platform controls and enforces an entire organization's security policies, offering operational simplification. This is a major improvement for IT teams, enabling them to move away from site-centric security to user-centric security.
- Overall simplicity of the network. There's no need for complex and expensive Multiprotocol Label Switching (MPLS) lines or network infrastructure. The entire network infrastructure is adapted to make it simple, maintainable and easy to consume -- regardless of where employees, data centers or cloud environments are located.
- Enhanced network security. Effective implementation of SASE services can protect sensitive data and help mitigate a variety of attacks, such as man-in-the-middle interceptions, spoofing and malicious traffic. Leading SASE services also provide secure encryption for all remote devices and apply more rigorous inspection policies for public access networks, such as public Wi-Fi. Privacy controls can also typically be better enforced by routing traffic to POPs in specific regions.
- Backbone and edge unification. SASE combines a single backbone with edge services, such as content delivery networks, CASBs, virtual private network replacement and edge networking. SASE lets a provider offer cloud, internet access, data center services, networking and security functions all through a single service -- as a joint effort across networking, security, mobile, app development and systems administration teams.
- Reduced costs. SASE is cost-effective because both network and security options are consolidated into one service. It eliminates the need for multiple security appliances and tools, reducing hardware, software and maintenance costs.
- Scalability. Depending on the network requirements, SASE can be easily scaled up or down. This offers the flexibility to add or remove services as needed.
- Improved hybrid working experience. SASE provides visibility and control in hybrid network environments where workers can work in the office, from home or in other remote locations. It also reduces end-user latency by routing traffic securely across on- and off-premises networks.
What are the challenges of SASE?
As the term SASE describes an emerging technology with variable approaches, drawbacks are nonspecific. However, the following challenges can sometimes be associated with SASE:
- Vendor lock-in. Generally speaking, the most significant potential drawbacks are that IT teams forfeit certain benefits of multisourcing, such as ensuring that various elements are sourced from the best possible providers for individual functions and diversifying risk in vendor operations.
- Single point of failure. With SASE architecture, users risk a single point of failure or exposure. As SASE delivers all networking and security functions together as a single service, technical issues on the provider side can potentially result in entire system shutdowns for end users.
- Integration issues. Since SASE represents a fundamental change in how networks and security are managed, it can sometimes be difficult to integrate existing and legacy systems with new SASE technology.
- Collaboration between network and security teams. Network and security functions should both collaborate on SASE deployments. However, in most organizations, security teams are frequently in charge of the process, and network technicians are usually only considered after the deployment process has already begun. This can sometimes cause conflicts in the process.
- Lack of industry standards. As SASE is still in its early stages -- the term first being coined in 2019 -- there's a lack of commonly accepted industry standards for deployment, security and performance.
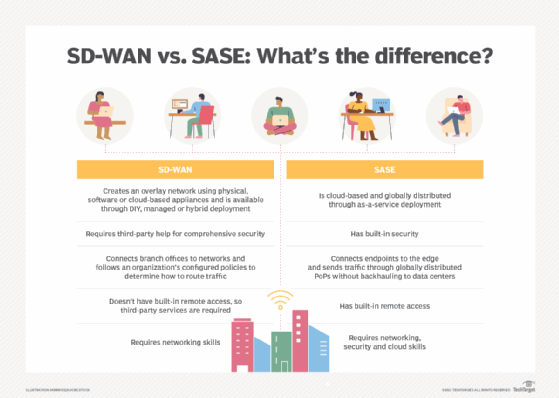
The difference between SASE and SD-WAN
Both SASE and SD-WAN are methods of connecting networks. SASE was originally gleaned from SD-WAN and incorporates its functionalities, but there are also some differences between the two.
SD-WAN is a networking technique that controls data delivery over a WAN. It enables companies to build dependable, affordable links across many sites by using a variety of network connections, including broadband internet, 4G and MPLS. These services come in both physical and cloud-based options, and although certain SD-WAN systems integrate a full security stack into their offerings, not all of them do.
While SASE and SD-WAN do share WAN connectivity features, the biggest difference between the two is that SASE also includes a collection of security services. SASE is primarily cloud-based and brings together WAN capabilities and network security services, including SWGs, CASBs and ZTNA, into a single offering. By combining networking and security operations into one cloud-delivered service, SASE can simplify and secure network access.
The future of SASE
SASE has the potential to become a key cloud security and optimization technology. Enterprises are becoming more interested in SASE, and research forecasted that usage of this technology will increase in the coming years. Gartner -- the company that first coined the term in 2019 – predicted that the SASE market will reach $25 billion by the year 2027, growing at a 29% compound annual growth rate.
Part of this growth rate might be due to SASE's reliability, low latencies and secure cloud connections.
SASE serves the needs of mobile workforces by combining networking and security capabilities. By lowering the number of providers IT teams require, this integration can help reduce complexity and cost. In addition, SASE enables a more efficient approach to delivering a secure digital workspace and can aid businesses in their digital transformation journey.
SD-WAN adoption necessitates extensive market research and analysis so that enterprises can understand what they require from their WANs. Explore SD-WAN vendor offerings, and see how they compare.







