
What is Simple Network Management Protocol (SNMP)?
Simple Network Management Protocol (SNMP) is an application-layer protocol for monitoring and managing network devices on a local area network or wide area network. SNMP provides network devices, such as routers, servers and printers, with a common language for sharing information with a network management system (NMS).
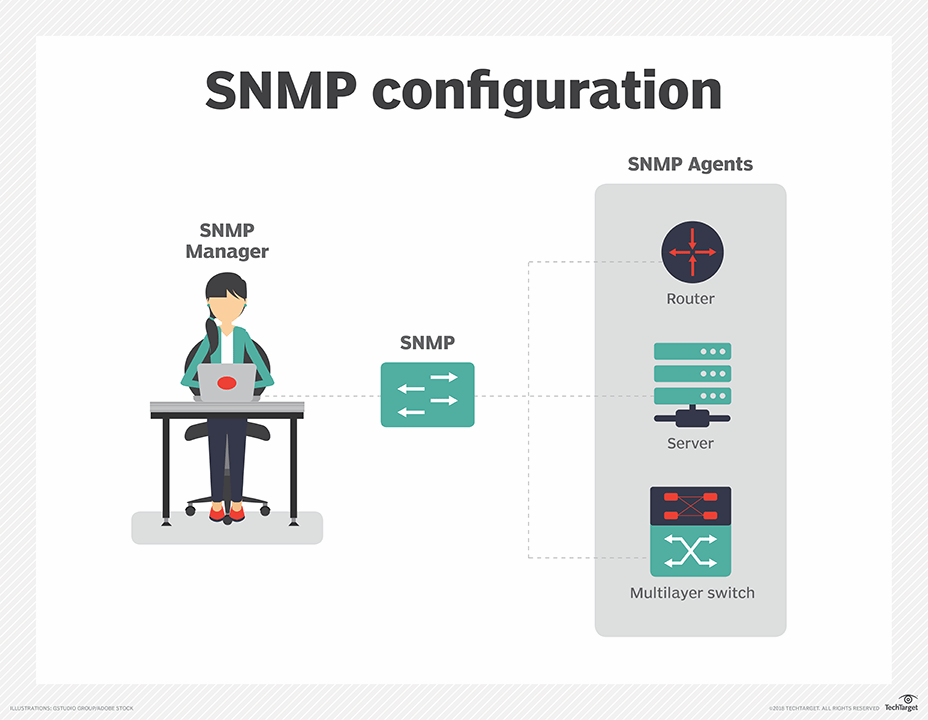
SNMP's client-server architecture has four components:
- An SNMP agent, which acts as the server.
- Managed network nodes, which are the devices and services on which the agents run.
- An SNMP manager, which acts as the client.
- A management information base (MIB), which acts as the server's database.
When the SNMP manager asks the agent a question, the agent uses the MIB to supply the answer.
SNMP is so popular that most network devices come prebundled with SNMP agents. However, to use the protocol, network administrators must first change their network devices' default configuration settings so SNMP agents can communicate with the NMS.
SNMP is part of the original Internet Protocol (IP) suite as defined by the Internet Engineering Task Force. Multiple versions of the SNMP protocol exist. The most recent version, SNMPv3, includes security mechanisms for authentication, encryption and access control.
What is SNMP used for?
SNMP is used in many different contexts throughout an enterprise:
- Monitoring and managing network devices. Network admins can use an SMNP-based central management system to communicate with managed devices and receive status reports.
- Performance monitoring. The protocol lets admins keep tabs on hardware devices that are spread out in an organization and susceptible to failure. SNMP monitoring of printers, uninterruptible power supply (UPS) units, servers, routers and other network devices is possible even when they're in different locations.
- Operational continuity. SNMP helps keep devices up and running. For instance, a printer might send error messages via SNMP, alerting staff to an issue before anyone attempts to use it. SNMP messages can also prevent a UPS failure during a power outage. In both examples, SNMP contributes to a business's operational continuity.
- Device security. SNMP also helps monitor for suspicious activity, protecting devices from various types of cyberattacks and other threats that can cause downtime. When a device sends an SNMP alert indicating such activity, staff members can act fast to tighten network security configurations.
How SNMP works
SNMP software agents on network devices and services communicate with an NMS to relay status information and configuration changes. The NMS provides a single interface from which administrators can issue batch commands and receive automatic alerts.
This article is part of
What is network management?
SNMP relies on the MIB concept to determine how device metric information is exchanged. The MIB is a formal description of a network device's components and status information.
MIBs can be created for any internet of things (IoT) network device, including IP video cameras, vehicles, and industrial and medical equipment. In addition to hardware, SNMP can be used to monitor services such as Dynamic Host Configuration Protocol.
SNMP uses a blend of pull and push communications between network devices and the NMS. The SNMP agent, which resides with the MIB on a network device, constantly collects status information. However, it only pushes information to the NMS upon request or when some aspect of the network crosses a predefined threshold known as a trap. Trap messages are typically sent to the management server when something significant happens, such as a serious error condition.
SNMP also includes an inform message type that enables a network monitoring tool to acknowledge messages from a device. Inform messages enable the agent to reset a triggered alert.
Network management tools can use a set message to change a network device through the SNMP agent. These predefined messages also enable the network manager to change device configurations in response to new network events.
In most cases, SNMP functions in a synchronous model. The SNMP manager initiates communications, and the agent responds. Typically, SNMP uses User Datagram Protocol as its transport protocol. Well-known UDP ports for SNMP traffic are 161 (SNMP) and 162 (SNMPTRAP). These two ports are fundamental defaults and are the same in all versions of SNMP.
SNMP is called simple because of the uncomplicated nature of the protocol's architecture. It can issue read/write commands, such as resetting a password or changing a configuration setting. It can also report back how much bandwidth, processing power and memory are in use.
As one of the most widely used protocols, SNMP is supported on an range of hardware -- from conventional network equipment, such as routers, switches and wireless access points, to endpoints, like printers, scanners and IoT devices.
SNMP versions
To date, there are three versions of SNMP, each with distinguishing capabilities and drawbacks:
- SNMPv1 focused on ease of use and simple setup. However, compared to subsequent protocol versions, it had limited capabilities and security measures. Any data exchanged between connected devices and the central management system was authenticated with just a plaintext password. This password was known as a community string that anyone with network access could see, including unauthorized users. Also, several messages were often needed to transmit large sets of information.
- SNMPv2, more commonly referred to as SNMPv2c, had more capabilities than version 1, but it adhered to the same flawed authentication method. On the positive side, SNMPv2c was able to send larger amounts of data faster, and it added a new form of communication called informs. While trap messages informed the management system of an error or issue, inform messages enabled an SNMP manager to acknowledge receipt of an SNMP agent's message. The agent kept sending the inform message until it got a response from the manager.
- SNMPv3 offers the most security, with enhanced mechanisms that ensure only authorized users can view SNMP messages. Unlike previous versions, version 3 also offers encryption, where SNMP messages are scrambled, and so unauthorized users can't read them. This version does require a more complex setup to configure the additional security measures. It also requires more resources for increased computing and memory use.
Key components of SNMP
The four main components in an SNMP-managed network are the following.
1. SNMP agent
Agent software runs on the hardware or service being monitored, collecting data about disk space, bandwidth use and other network performance metrics. The agent sends information back to the management system in response to SNMP manager queries. An agent might also proactively notify the NMS if an error occurs. Most devices come with an SNMP agent preinstalled, but it typically needs to be turned on and configured.
2. SNMP-managed network nodes
These are the network devices and services on which the agents run.
3. SNMP manager
This NMS is a software platform that functions as a centralized console to which agents feed information. The NMS actively requests that agents send updates at regular intervals. What a network manager can do with that information depends on how feature-rich the NMS is.
There are several free SNMP managers available, but they're typically limited in their capabilities and the number of nodes they support. At the other end of the spectrum, enterprise-grade platforms offer advanced features for more complex networks, with some products supporting up to tens of thousands of network nodes.
4. Management information base
This MIB database is a text file (.mib) that itemizes and describes all managed objects on a particular device that can be queried or controlled using SNMP. Each MIB item is assigned an object identifier (OID).
SNMP commands
SNMP can perform a multitude of functions, using a blend of push and pull communications between network devices and the management system. These include issuing read/write commands and providing updates on bandwidth, processing power and memory use. Some SNMP managers automatically send the administrator an email or text message alert when a predefined threshold is exceeded.
These commands and messages -- typically transported over UDP or Transmission Control Protocol/IP, or TCP/IP -- are known as protocol data units. Common SNMP commands include the following:
- GET request. The SNMP manager generates and sends this to an agent to obtain the value of a variable, identified by its OID in an MIB.
- GETBULK request. The SNMP manager sends this to the agent to obtain a potentially large amount of data, especially large tables.
- GETNEXT request. The SNMP manager sends this to the agent to retrieve the values of the next OID in the MIB's hierarchy.
- INFORM request. This is an asynchronous alert similar to a trap message but requires the SNMP to confirm receipt.
- RESPONSE. The agent sends this to the SNMP manager, issued in reply to a GET request, GETNEXT request, GETBULK request or SET Rrequest. It contains the values of the requested variables.
- SET request. The SNMP manager sends this to the agent to issue configurations or commands.
- TRAP. The agent sends this to the manager as an asynchronous alert, indicating that a significant event, such as an error or failure, has occurred.
SNMP is one of various network protocols used to protect IT infrastructure. Learn about other common network protocols and their functions.







