application delivery controller (ADC)
What is an application delivery controller (ADC)?
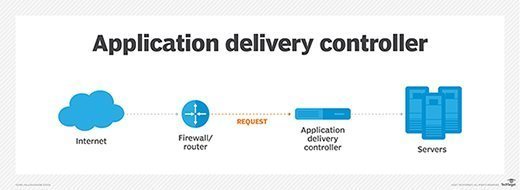
An application delivery controller (ADC) is a network component that manages and optimizes how client machines connect to web and enterprise application servers. In general, a controller is a hardware device or a software program that manages or directs the flow of data between two entities.
An ADC performs load balancing between servers and accelerates applications. As the technology has evolved, newer ADC offerings have expanded functions that surpass traditional load balancers and first-generation ADCs, such as Secure Sockets Layer/Transport Layer Security (SSL/TLS) offloading, rate shaping and firewalls for web applications.
How application delivery controllers work
An ADC essentially functions as a load balancer. It optimizes end-user performance, reliability, data center resource use and security for enterprise applications. But ADCs also perform other functions, such as the following:
- Application acceleration.
- Caching.
- Compression.
- Traffic shaping.
- Content switching.
- Multiplexing.
- Application security.
An ADC accelerates the performance of applications delivered over the wide area network by implementing optimization techniques, such as application classification, compression and reverse caching.
Typically, an ADC is placed behind a firewall and in front of one or more application servers. It acts as a single point of control that can determine the security needs of an application and provide simplified authentication, authorization and accounting.
ADC features
An ADC can be deployed physically as a hardware appliance or virtually as software, running on an x86 server. Virtual ADCs are particularly useful in large enterprise data centers and cloud computing environments where customers need to be able to scale capacity up and down as application demand fluctuates. These systems also increasingly offer virtualization support, multi-tenancy and forms of central authentication.
Load balancing
ADCs provide Layer 3, 4 and 7 load balancing. In Layers 3 and 4, traffic is distributed based on subnets and IP addresses, TCP session information, protocols and port numbers. Layer 7 capabilities include content load balancing, which distributes traffic based on URL, domain, HTTP header or query. ADCs vary based on the ability to support different applications.
Monitoring
ADCs alternate connections between devices using methods such as round robin, response time or least packets. Modern ADCs use monitoring to determine the health of a server, which is an important step before sending traffic that otherwise might reach an overloaded server. ADC monitoring uses many protocols, including domain name system (DNS), File Transfer Protocol, HTTP, HTTP Secure, TCP, User Datagram Protocol and others.
Multiplexing
By carrying out TCP multiplexing, ADCs compress the number of TCP sessions to save network bandwidth, sending multiple signals at the same time. Multiplexing is beneficial for application servers because device load and exchange traffic grow exponentially with new sessions.
Protocol integration
Most ADCs also support integration with the existing network and dynamic routing protocols, such as Open Shortest Path First, Border Gateway Protocol and Virtual Extensible LAN. Additionally, ADCs can take the SSL/TLS processing load off servers, accelerate applications and maintain high availability.
ADC security
ADCs play an important role in network security. Among other benefits, they provide a first line of defense against distributed denial-of-service (DDoS) attacks. ADCs use techniques such as firewall load balancing, intrusion prevention and detection, and web application firewalls (WAFs) to handle DDoS attack traffic and keep that traffic from flooding servers.
In other cases, ADCs can terminate SSL/TLS tunneling attacks. Some ADCs come with a DNS application firewall to stop a sudden influx of traffic to a DNS server.
WAFs are also used to stop cross-site scripting. Depending on the vendor, this feature might be offered as a built-in feature with the ADC license or a special add-on. WAFs can disrupt Structured Query Language injections, eliminate cookie poisoning and protect access to sensitive data.
Some ADCs also offer data loss protection. With this feature, the ADC inspects data to determine if it meets company policies, flagging or blocking data that is malicious or a violation of those policies.
Pros and cons of ADCs
ADCs provide application load balancing, secure application delivery and manage application behavior. They can be installed as hardware or virtualized software, giving enterprises additional flexibility in how they are deployed. They also support the use of dedicated microservices within enterprise environments by managing the internal data traffic generated by these services.
Recent ADC enhancements include support for containerized applications and comprehensive analytics. These upgrades enable enterprises to manage traffic flows within their operations more efficiently. As a result, ADCs offer many more features and improved performance.
As for disadvantages, ADC features are proprietary, so it can be challenging for enterprises to compare ADC offerings. Each ADC processes traffic differently, which might cause performance bottlenecks and other operational issues. Decrypting and offloading SSL/TLS traffic can also consume significant resources.
Editor's note: This definition was written originally by Eamon McCarthy Earls and updated by editors to improve reader experience.