gatekeeper
What is a gatekeeper?
A gatekeeper is a management tool for H.323 multimedia networks. Its primary functions are to convert phone numbers to IP addresses for VoIP and provide interoperability between different networks. Gatekeepers are available as either hardware devices or software applications, and are offered as proprietary products from a number of vendors, including Cisco and Symantec, or as freeware.
What does a H.323 gatekeeper do?
A single gatekeeper controls interactions for each zone, which comprises the terminals, multipoint control units (MCU), and gateways within a particular domain. Although the gatekeeper is an optional component, when it is included, it becomes the central administrative entity.
Depending on the demands of the specific network, the gatekeeper oversees authentication, authorization, telephone directory and private branch exchange (PBX) services, as well as call control and routing. Other functions may include monitoring the network for load balancing and real-time network management applications, intrusion detection and prevention and providing interfaces to legacy systems.
Gatekeeper functions
A gatekeeper provides a variety of functions. Required functions include:
- Address translation. The gatekeeper translates telephone numbers and H.323 IDs to endpoint IP addresses.
- Admission control. The gatekeeper an endpoint's admission into the H.323 network.
- Bandwidth control. The gatekeeper manages endpoint bandwidth requirements.
- Zone management. The gatekeeper manages the zone for all registered endpoints in that zone.
A gatekeeper may also provide these optional functions:
- Call security. A gatekeeper might authenticate and authorize calls.
- Call management. The gatekeeper keeps information about the state endpoints to indicate when they are busy or to redirect calls.
- Bandwidth management. When the required bandwidth is not available for a call, the gatekeeper can reject admission.
- call control signaling. The gatekeeper can reroute a call so that endpoints communicate directly.
Gatekeeper design
Gatekeepers can be implemented in either a peer-to-peer or hierarchical structure.
Neighbor gatekeepers are arranged in a single-tier peer-to-peer manner. A gatekeeper is installed at each site and manages its own zone. Inter-zone communications are routed directly between zones and controlled based on the relationship between each gatekeeper. This approach is typically adopted by multi-site companies.
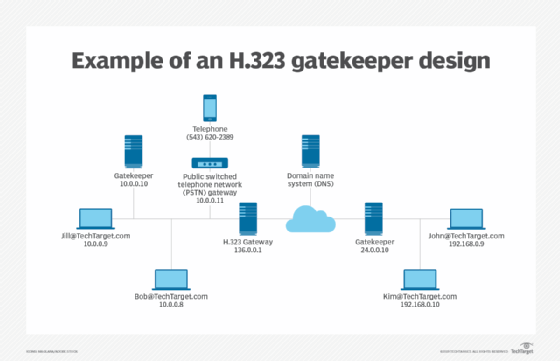
Directory gatekeepers are implemented in a multi-tier design. Like neighbor gatekeepers, each directory gatekeeper manages its own zone. However, inter-zone communicates are indirectly routed between zones.
Directory gatekeepers route inter-zone communications through the appropriate parent-child gatekeepers. A directory gatekeeper only knows its "child" and "parent" gatekeepers. If a gatekeeper doesn't know the zone of a dialed number, it routes the call to its parent gatekeeper. That parent gatekeeper searches its database to determine if it knows the zone. If it does not know the zone, then that parent routes the call to its parent. This pattern continues until the call reaches a parent gatekeeper with a child gatekeeper that matches the zone. The call is then routed through each child directory gatekeeper until it reaches the appropriate endpoint.