
carloscastilla - Fotolia
What are the risks of third-party VPN services?
IP address leaks, DNS service leaks and WebRTC transmissions could expose your online activities if you use certain unreliable third-party VPN services.
The significant increase in work-from-home policies during the pandemic has put a spotlight on third-party VPN services. While several services can provide an extra layer of encryption and anonymity when using the internet, you'll need to consider some third-party VPN risks depending on the service you choose.
Third-party VPN services work by installing software, a browser plugin or a security hardware appliance between end devices and the internet. A VPN tunnel is then established between the end-user device and the service provider's VPN endpoint on the internet. Once the VPN tunnel is established, internet-bound traffic is encrypted across the tunnel and routed to the third-party provider's network.
From there, the provider will translate your originating source IP address to one of its own IP addresses and transmit the internet packets to their destination on your behalf. Hiding your source IP from the rest of the internet means destination servers cannot track or log the true source of the request.
What are the dangers of third-party VPNs?
One major third-party VPN risk occurs when the service provider does not properly hide your originating IP address as intended. This is known as an IP address leak. When this occurs, the servers or devices you're communicating with on the internet can determine you are the source of the generated traffic -- and not the VPN service provider. Thus, the tracking of online behavior is no longer hidden.
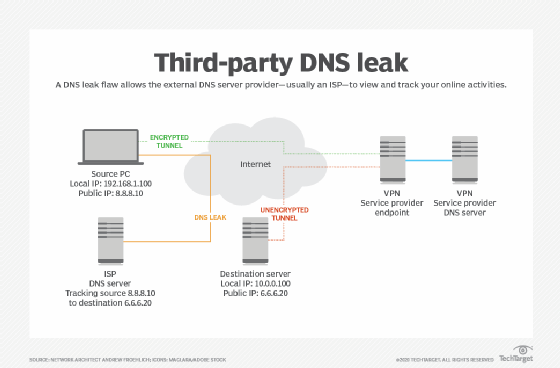
Another type of leak involves DNS services. Most third-party VPN service providers offer their own DNS servers to perform lookups. This is important because it enables DNS queries through the encrypted tunnel -- as opposed to outside the tunnel where they could be intercepted or logged. A DNS leak flaw allows the external DNS server provider -- usually an ISP -- to view and track your online activities.
Third-party VPN risks can also surface with Web Real-Time Communications (WebRTC) services. WebRTC is a framework that governs real-time communications, such as audio and video streaming. When a WebRTC session is transmitted across a VPN service, the browser may try to bypass the VPN tunnel and instead point directly to the destination RTC server, once again exposing or leaking your true IP address.
The inherent vulnerabilities of any third-party VPN service are only part of the equation. You must also consider the trustworthiness of the provider itself. As the saying goes, "You get what you pay for." This is especially true for VPN services that are offered for free or at low cost. In these situations, the software could do the following:
- Secretly collect personal information from your PC or smart device due to excessive permissions granting requirements. This information is then sold to the highest bidder.
- Create, store and potentially sell or share internet activity logs.
- Have malware planted inside.
Therefore, be sure the third-party VPN service provider you work with has a good reputation -- both within the industry and in the specific countries in which you primarily conduct business.
Finally, the type of VPN service you choose will determine your level of privacy and security. For example, beware of web browser plugins that claim they are VPNs. Instead, they operate as a web proxy that only masks your IP address.
Dedicated VPN software will establish a true VPN tunnel that's encrypted -- but only if the user manually enables it. The most secure third-party VPN services are those that are hardware-based. The hardware establishes an always-on encrypted tunnel and protects all devices that are deployed behind the VPN hardware. The downside, of course, is: Once you move your smartphone or laptop to a different location, the VPN services -- and their inherent protection -- don't go along with you.








