man-in-the-middle attack (MitM)
What is a man-in-the-middle (MitM) attack?
A man-in-the-middle (MitM) attack is a type of cyber attack in which the attacker secretly intercepts and relays messages between two parties who believe they are communicating directly with each other. The attack is a type of eavesdropping in which the attacker intercepts and then controls the entire conversation.
MitM cyber attacks pose a serious threat to online security because they give the attacker the ability to capture and manipulate sensitive personal information -- such as login credentials, account details or credit card numbers -- in real time.
MitM attacks are also sometimes referred to as monster-in-the-middle, machine-in-the-middle, monkey-in-the-middle and man-in-the-browser attacks. Man-in-the-browser is the most common type of MitM attack in which the attackers focus on browser infection and inject malicious proxy malware into the victim's device. The malware is commonly introduced through phishing emails. The main objective behind these attacks is to steal financial information by intercepting a user's traffic to a banking or financial website.

How do MitM attacks work?
During MitM attacks, cybercriminals insert themselves in the middle of data transactions or online communication. Through the distribution of malware, the attacker gains easy access to the user's web browser and the data it sends and receives during transactions. Online banking and e-commerce sites, which require secure authentication with a public key and a private key, are the prime targets of MitM attacks as they enable attackers to capture login credentials and other confidential information.
Typically, these attacks are carried out through a two-step process known as data interception and decryption. Data interception entails an attacker intercepting a data transfer between a client and a server. The attacker tricks the client and the server into believing that they are exchanging information with each other, while the attacker intercepts the data, creates a connection to the real site and acts as a proxy to read and insert false information into the communication.
The following steps are involved in a common data interception technique:
- An attacker installs a packet sniffer to gauge any network traffic that might be insecure, such as a user accessing a Hypertext Transfer Protocol (HTTP)-based website or using a non-secure public hotspot.
- Once the user logs into the insecure website, the attacker retrieves the user's information and redirects them to a fake website.
- The fake website mimics the original website and gathers all the pertinent user data, which the attacker can then use to access all the user resources on the original website.
The decryption phase is where the intercepted data is unencrypted. This essential step enables the attacker to finally decipher and use the data to their advantage; for example, they can carry out identity theft or cause disruptions to business operations.
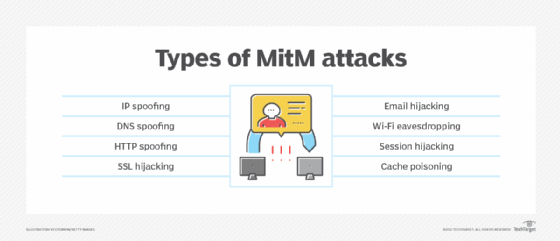
What are the types of man-in-the-middle attacks?
To gain access to devices and sensitive information, cybercriminals use the following ways to conduct MitM attacks:
- Internet Protocol spoofing. Like identity theft, IP spoofing takes place when cybercriminals alter the source IP address of a website, email address or device for the purpose of masking it. This dupes the users into believing that they are interacting with a legit source and the sensitive information they share during the transaction gets transferred to the cybercriminals instead.
- Domain Name System spoofing. This is a type of man-in-the-middle attack where cybercriminals alter domain names to redirect traffic to fake websites. Users might think that they are reaching a secure and trusted website, but instead, they land on a website operated by cybercriminals. The main aim behind DNS spoofing is to reroute traffic to a fake website or to capture user login credentials.
- HTTP spoofing. The HTTP protocol is the embodiment of secure internet communications. HTTPS indicates a safe and trusted website. During an HTTPS spoofing attack, a browser session is redirected to an unsecured or HTTP-based website without the user's knowledge or consent. Cybercriminals can monitor user interactions and steal shared personal information through this redirection.
- Secure Sockets Layer hijacking. SSL is a protocol that establishes an encrypted connection between a browser and the web server. During SSL hijacking, a cybercriminal might use another computer and a secure server to intercept all information traveling between the server and the end user's computer.
- Email hijacking. This is a type of MitM attack where cybercriminals gain control of email accounts of banks and other financial institutions to monitor any transactions that users conduct. Cybercriminals may even spoof the bank's email address and send instructions to customers that lead them to unknowingly transfer their money to the cybercriminals.
- Wi-Fi eavesdropping. This MitM attack is one of the many risk factors posed by public Wi-Fi. During this attack, public Wi-Fi users get tricked into connecting to malicious Wi-Fi networks and hotspots. Cybercriminals accomplish this by setting up Wi-Fi connections with names that resemble nearby businesses.
- Session hijacking. Also known as stealing browser cookies, this malicious practice takes place when cybercriminals steal personal data and passwords stored inside the cookies of a user's browsing session. Sometimes, cybercriminals can gain endless access to users' saved resources. For example, they might steal users' confidential data and identities, purchase items or steal money from their bank accounts.
- Cache poisoning. Also known as Address Resolution Protocol, or ARP cache poisoning, this popular modern-day MitM attack enables cybercriminals who are on the same subnet as the victims to eavesdrop on all traffic being routed between them.
How to prevent man-in-the-middle attacks
Mitigation is the best defense against MitM attacks. The following highlights a few ways these attacks can be prevented:
- Secure connections. This is the first line of defense against MitM attacks. Users should only visit websites that show "HTTPS" in the URL bar, instead of just "HTTP". Most browsers display a padlock sign before the URL, which indicates a secure website. Besides ensuring website security, it is also important to avoid using unsecured public Wi-Fi connections, as they are susceptible to attacks and interception by cybercriminals. Organizations should enforce multifactor authentication across the board, as it adds an additional layer of security to online communications.
- Avoid phishing emails. Cybercriminals purposely craft phishing emails to trick users into opening them. Users should think twice before opening emails coming from unverified or unknown sources. Phishing emails often look like they come from a legit source, such as a bank account or a financial institution. These emails might ask users to click on a link to enter their login credentials or update passwords. Clicking on these links should be avoided, as they might redirect a user to a fake website or download malicious software on their device.
- Virtual private network encryption. A VPN encrypts internet connections and online data transfers, such as passwords and credit card information and should be used when connecting to insecure public Wi-Fi networks and hotspots. A VPN can ambush a potential man-in-the-middle attack. Even if a cybercriminal manages to access a network, they will not be successful in deciphering the messages or accessing resources due to the encryption provided by the VPN. Organizations should also ensure their employees are logging into the company through a secure corporate VPN, especially if they are working remotely.
- Endpoint security. Implementing comprehensive endpoint security is paramount when trying to prevent the spread of malware and other cyber attacks. Because MitM attacks use malware for execution, it is important to have antimalware and internet security products in place.
- Most cyber attacks are unknowingly initiated by human behavior. By educating users on the dangers of a MitM attack and implementing mandatory proactive security awareness training for employees, organizations can preemptively safeguard their sensitive data. The training should also teach users how to spot malicious emails, and enlighten them regarding security best practices, such as implementing a VPN, avoiding public Wi-Fi networks and not clicking on suspicious email links.
Examples of man-in-the-middle attacks
While the history of MitM attacks dates back to pre-internet times, they have gained the most traction and limelight in recent years. The following are a few popular real-world examples of man-in-the-middle attacks:
Equifax's mobile application. One of the largest credit reporting agencies, Equifax suffered a massive data breach in 2017 that leaked the financial information of nearly 150 million people in the U.S. This breach was caused by Equifax's failure to patch a known vulnerability. Along with this breach, it was also discovered that the company's mobile phone apps were not always using HTTPS, enabling hackers to intercept the data of Equifax users as they accessed their accounts.
Superfish. In 2015, Lenovo computers were shipped out with pre-installed adware that made users vulnerable to MitM attacks. This software, known as Superfish Visual Search, inserted advertisements into a user's encrypted web traffic. An updated release of Microsoft Windows Defender in February 2015 removed this vulnerability.
DigiNotar. A Dutch issuer of digital security certificates, DigiNotar was breached in 2011 when a threat actor gained access to 500 certificates for prominent websites, such as Google and Skype. The threat actor employed the tactics of an MitM attack by tricking users into entering passwords on fake websites posing as the real ones. DigiNotar ultimately filed for bankruptcy to recover from the losses of this data breach.
Mobile devices are increasingly becoming the target for phishing and other cybersecurity threats. Learn what's causing this rise in mobile phishing attacks and how IT teams are identifying and mitigating these threats.







